1. 创建服务
- 最新dashboard(2.5.1)
# 创建dashboard服务
wget https://raw.githubusercontent.com/kubernetes/dashboard/master/aio/deploy/recommended.yaml
kubectl apply -f recommended.yaml
#创建列表
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
# 查看资源,是否准备好:
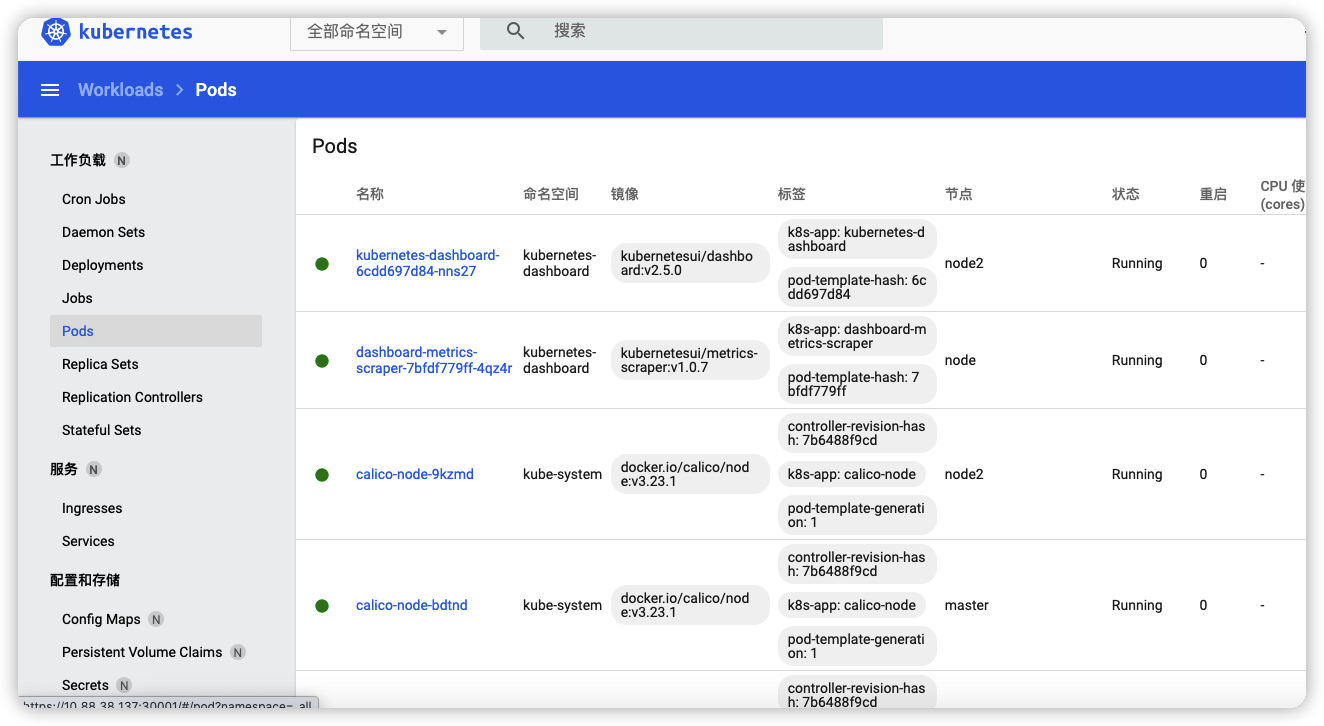
[root@master kubeadm_init]# kubectl get po -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-7bfdf779ff-4qz4r 1/1 Running 0 23h
kubernetes-dashboard-6cdd697d84-nns27 1/1 Running 0 23h
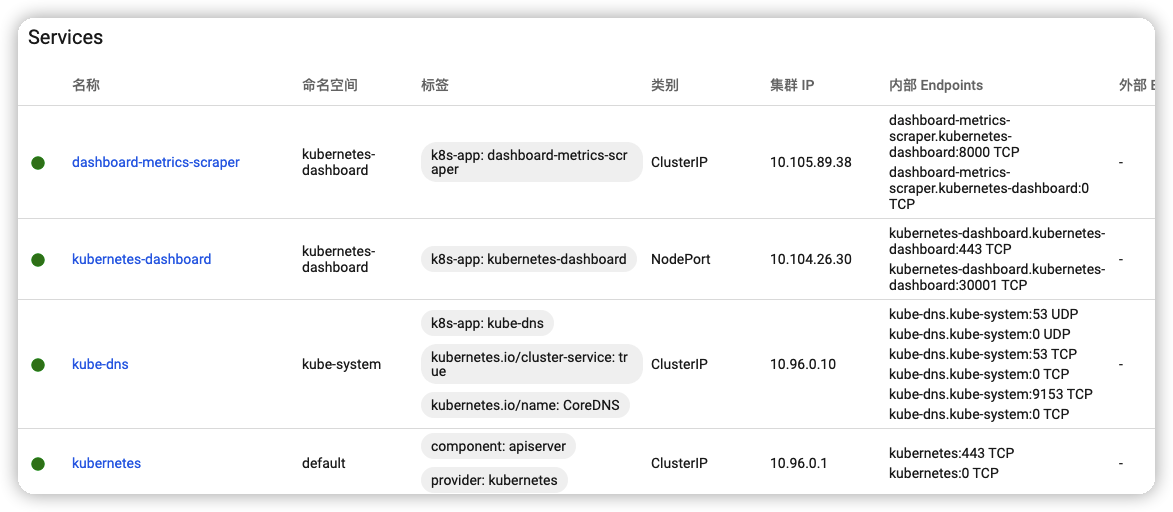
#查看服务
[root@master kubeadm_init]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.105.89.38 <none> 8000/TCP 23h
kubernetes-dashboard ClusterIP 10.104.26.30 <none> 443/TCP 23h
#查看
[root@master kubeadm_init]# kubectl get sa -n kubernetes-dashboard
NAME SECRETS AGE
default 0 23h
kubernetes-dashboard 0 23h
2. 修改端口配置
kubectl edit svc kubernetes-dashboard -n kubernetes-dashboard
#修改配置
apiVersion: v1
kind: Service
metadata:
spec:
clusterIP: 10.104.42.244
clusterIPs:
- 10.104.42.244
externalTrafficPolicy: Cluster
internalTrafficPolicy: Cluster
ipFamilies:
- IPv4
ipFamilyPolicy: SingleStack
ports:
- nodePort: 30001 # 自定义的外部端口(30000+)
port: 443
protocol: TCP
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
sessionAffinity: None
type: NodePort # 改为NodePort
status:
loadBalancer: {}
查看是否更新充许外部访问:
[root@master kubeadm_init]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.105.89.38 <none> 8000/TCP 23h
kubernetes-dashboard NodePort 10.104.26.30 <none> 443:30001/TCP 23h
创建访问令牌
查看recommended.yaml, 其中已包含了ServiceAccount, ClusterRoleBinding项,即默认的「用户」和「角色」。
- 但是我是菜鸟,使用默认的进去发现没有权限查看命名空间。也不知道怎么改,所以还是通过官方自定义角色。
创建自定义角色yaml文件:
tee dashboard-adminuser.yaml << EOF
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard
EOF
部署自定义角色:
kubectl apply -f dashboard-adminuser.yaml
#下面是创建列表
serviceaccount/admin-user created
clusterrolebinding.rbac.authorization.k8s.io/admin-user created
创建token
kubectl -n kubernetes-dashboard create token admin-user
#下面会出现token
eyJhbGciOiJSUzI1NiIsImtpZCI6IjhJcTVXcEpyY0oyNEUyN1lEcklxVFRfaTBJOXNmN05qbWVrTXR1NmpVOXcifQ.eyJhdWQiOlsiaHR0cHM6Ly9rdWJlcm5ldGVzLmRlZmF1bHQuc3ZjLmNsdXN0ZXIubG9jYWwiXSwiZXhwIjoxNjUzNDY2ODU3LCJpYXQiOjE2NTM0NjMyNTcsImlzcyI6Imh0dHBzOi8va3ViZXJuZXRlcy5kZWZhdWx0LnN2Yy5jbHVzdGVyLmxvY2FsIiwia3ViZXJuZXRlcy5pbyI6eyJuYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsInNlcnZpY2VhY2NvdW50Ijp7Im5hbWUiOiJhZG1pbi11c2VyIiwidWlkIjoiMjkxMDUwOWMtMDFlZi00NzFhLThhMzQtMjQ0MmEyNzM4Yzc5In19LCJuYmYiOjE2NTM0NjMyNTcsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDphZG1pbi11c2VyIn0.njCN9ZYVHnbjfTSln95CS0oveQpToqHe8HrMs6RQ1H--_l1U9e-qBt_KV-kD_Gi12huE1nkXdProPsnS2dDpV4AmxGihhKwAIBpbztKImOxVX8ecb_RnY04Hcf_axhPB7D8izZGbv0EbN-_BDvJaWteU0cBa0uOZ6-Cg8yND7T19Bh5ioC9ex-9-EIcNAyS4JEz8XuV_dGApI7jBORm_8I6JTfHqMrAtC4m-N5htMmCZQX6Cul39Uy330eTLTbpF6xRoF_32BP6YuPQ5gnk-52qzyHdzGNVFSxPMOP1KLkNATltNgbo8AUqH3mmVq5zPBB_sYvjxbQFOG_yEwZYtPA
访问测试
访问步骤
- 访问任意集群节点, 如:https://10.0.0.11:30001
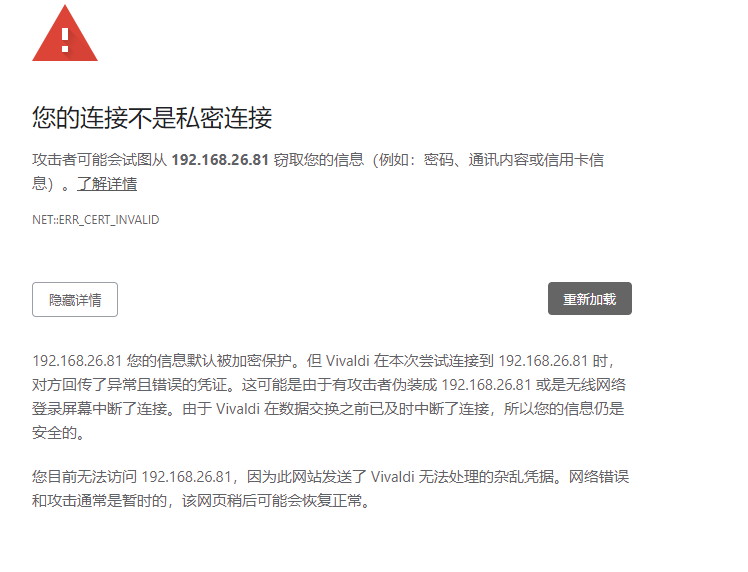
如果用新版的谷歌浏览器会提示这个报错,解决办法为,键盘直接输入thisisunsafe就可以了
- 第一次访问会有如下页面
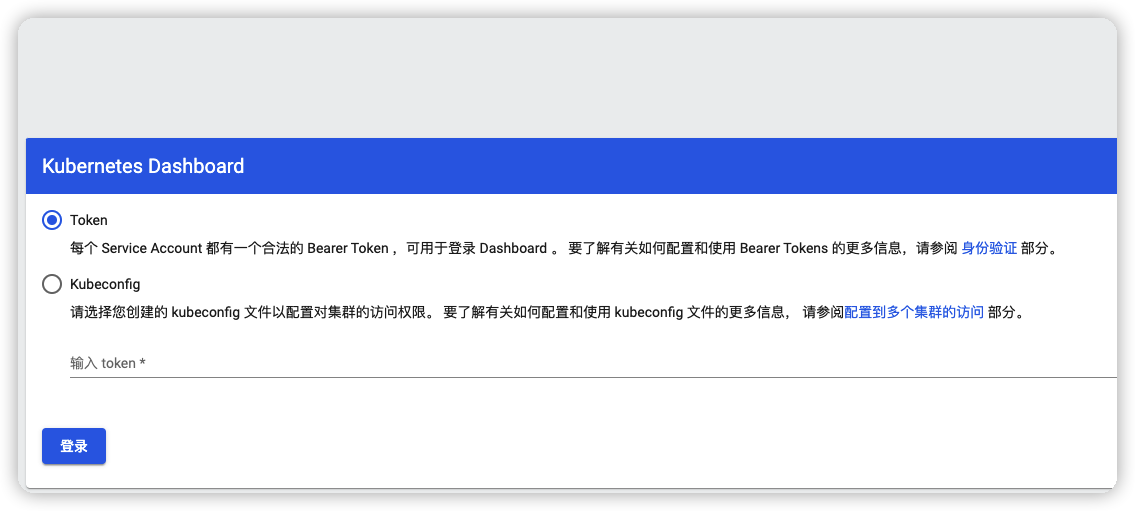
- 选择Token
粘贴上面创建的Token 进行登陆。
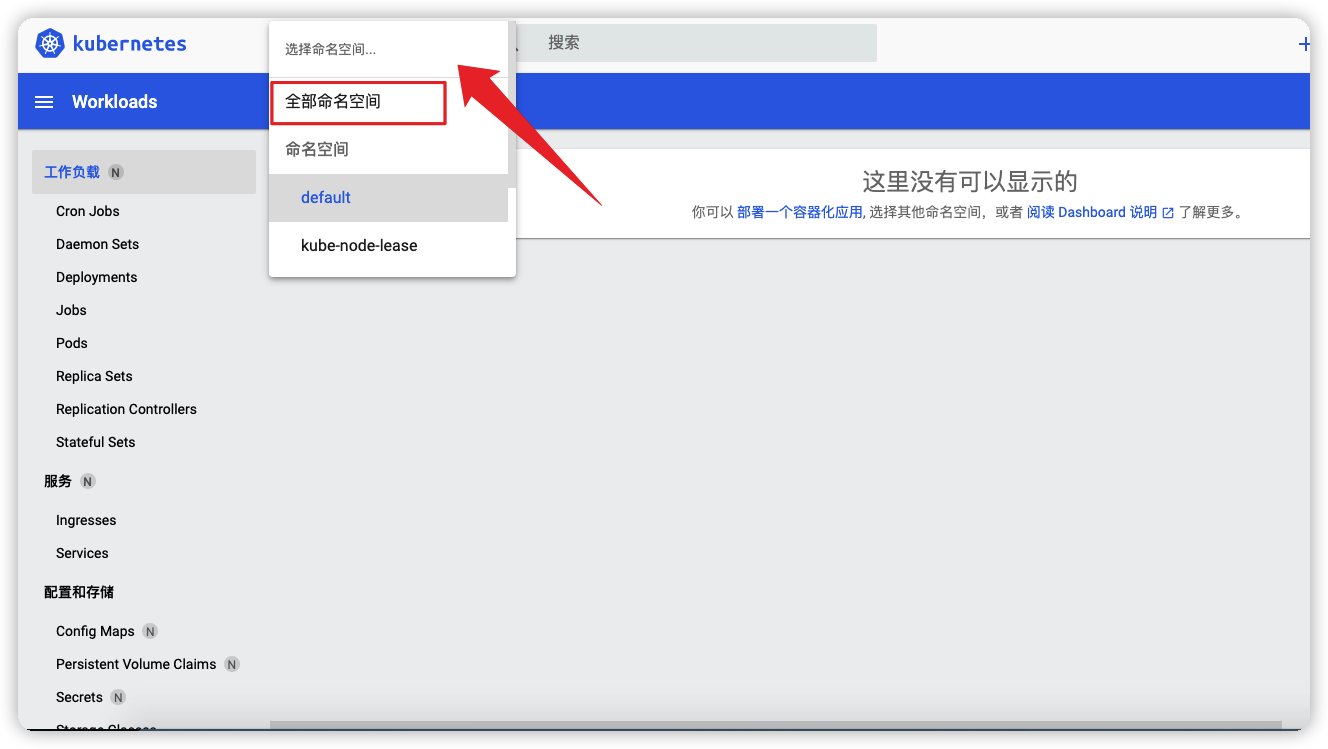
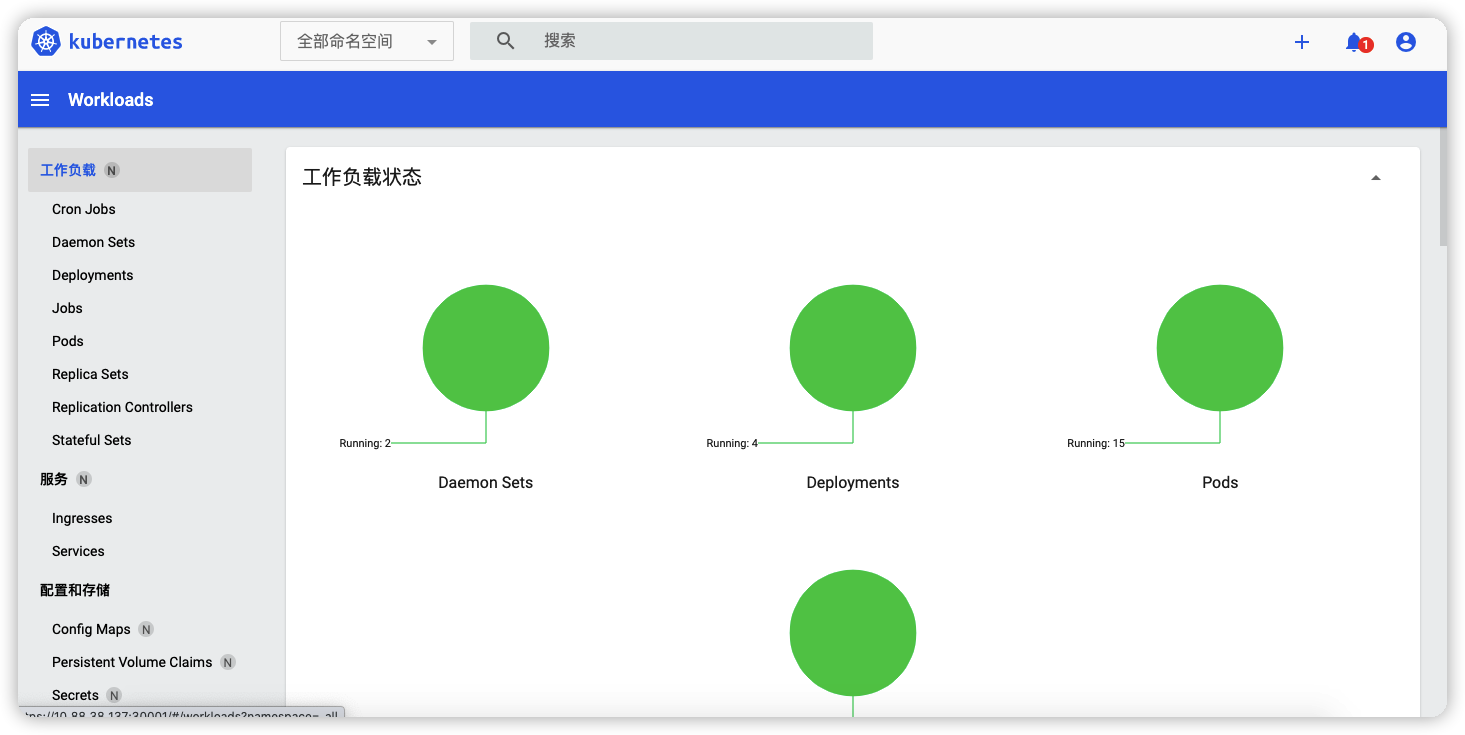
选择所有命名空间就可以查看相关信息



评论区